Using DNSSEC
Category: DNS
Created: 2015-06-25
Updated: 2020-08-18
Since version 1.8.2, LiveConfig supports DNSSEC. This means that cryptographic checksums are generated for domain data in order to protect them against modifications during transmission.
The most important components at DNSSEC are:
- Resource Records (RRs): these are the actual DNS user data (i.e. A/AAAA/MX/CNAME entries, etc.).
- RRSIG: special resource records that contain a checksum of the resource records to be protected (A/AAAA/MX/CNAME/etc.)
- Zone Signing Key (ZSK): RSA key pair with which the RR signatures (RRSIG) are generated. Since these signatures have to be calculated for verification very often, a relatively short RSA key is usually chosen (e.g. 1024 bits). The Zone Signing Keys should only be valid for a short period of time (1-3 months).
- Key Signing Key (KSK): RSA key pair with which the Zone Signing Keys are signed. These keys are larger (e.g. 2048 bits). These close the signature chain between the domain and the resource records - the public key must therefore be stored in the DNS for the respective top-level domain (as described below). Since the update is relatively complex, these keys are valid for a longer period (e.g. 1-2 years).
LiveConfig allows the automated signature of domains with NSEC3 Resource Records (according to RFC5155). If you enable DNSSEC for a domain in LiveConfig, the following happens:
- LiveConfig automatically creates an NSEC3PARAM resource record - these are the signature parameters required for NSEC3 (in particular a random value/“salt” for the checksums).
- LiveConfig writes the key signing key in a special directory to which the name server software (BIND) has access. BIND in turn automatically generates a zone signing key, includes KSK and ZSK in the zone (DNSKEY RRs) and signs all existing resource records.
- BIND independently updates the zone signing keys and signs them with the existing key signing key. The rotation of the ZSKs takes place completely automatically.
- All changes to the zone (e.g. after adding or editing your own DNS entries via LiveConfig) are also automatically signed.
With this procedure, dynamic zone changes are carried out and signed promptly and automatically, without having to manually generate, sign and load the entire zone again and again. The zone changes including the new signatures are transmitted to the slave servers by automated zone transfers (AXFR/IXFR).
Requirements
- At least the primary name server must be managed by LiveConfig. (One or more secondary DNS can also be “external”, e.g. from the domain registrar)
- All name servers (primary and all secondaries) must support DNSSEC.
- A hidden primary configuration is easily possible with DNSSEC.
- A name server cannot simultaneously be authoritative DNS and resolver for the same DNSSEC domain (this is not possible with the DNSSEC protocol due to the query flags); however, it is recommended to operate resolvers separately and on a dedicated basis anyway.
Enabling DNSSEC
If the primary DNS of the selected DNS template supports DNSSEC, you automatically have the option of activating DNSSEC when adding a domain (under Customers -> Domain or My Hosting -> Domains). To do this, you need to generate a Key Signing Key (KSK). Please create only one KSK - you only need several keys during a key exchange (key rollover); every unnecessary key increases the computational effort for the signature as well as the data volume generated by the DNS and thus also the DNS requests.
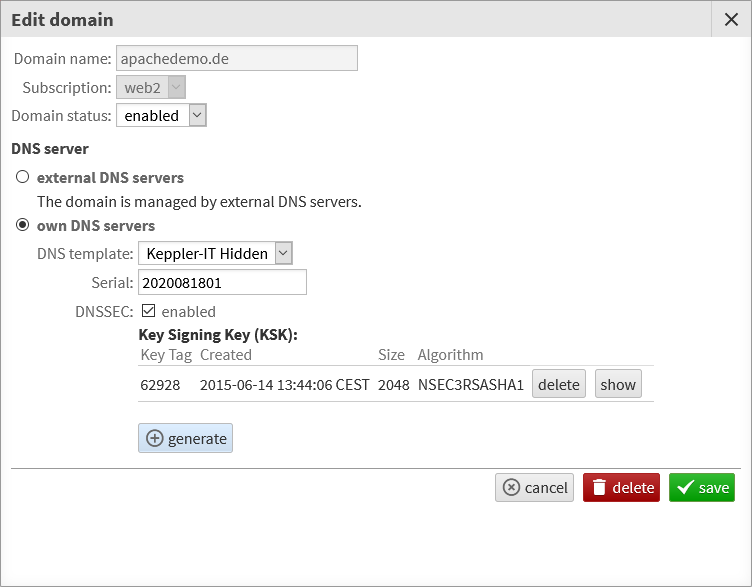
After the domain including the KSK has been saved, you can open it again for editing and display the KSK (this ensures that the KSK has actually been saved):
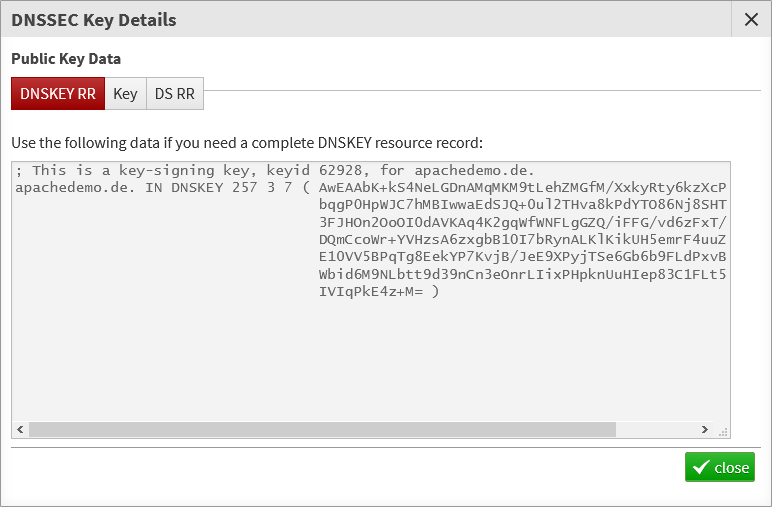
Finally you need to publish the KSK’s public key at your domain provider, often by creating a so-called Delegation Signing Resource Record (DS record). Make sure you select RSASHA1-NSEC3-SHA1 as the algorithm.
Example: managing DS record with InterNetX’ AutoDNS